Yesterday a critical security vulnerability has been published by Qualys concerning the GNU Library C (glibc), named GHOST.
Recent Articles
-

At Ikoula, the year is ending with a fresh start! We are excited to announce a major update to our range of dedicated servers. This revamp includes not only new configurations and optimized performance, but also a significant price reduction on several models. And to top it off, we've simplified our naming system to make our offers more accessible and clearer for you, our valued customers!
-

Explore the behind-the-scenes of Ikoula’s 25 years of expertise in web hosting and cloud services through the latest article published in le Figaro Partner. In this article, Joaquim dos Santos, R&D Director, details Ikoula’s offerings and bespoke cloud solutions tailored to every company, from SMEs to large enterprises. Discover how our personalized approach, commitment to security, and continuous expertise add value to businesses, while integrating a strong eco-responsible dimension that shapes our vision for a more sustainable future. -
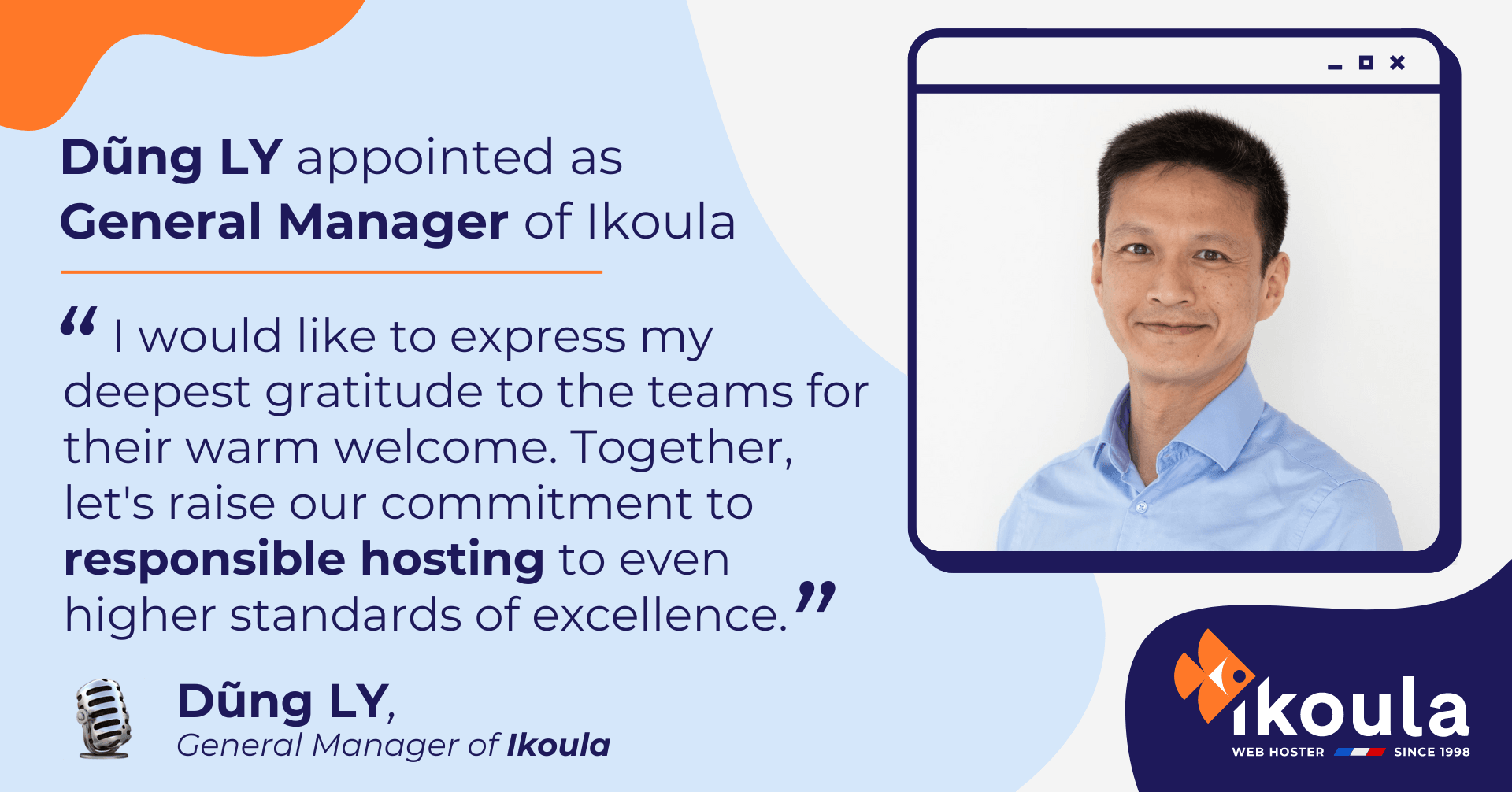
Ikoula, a French provider of IT hosting and outsourcing solutions since 1998, is pleased to announce the appointment of Dũng LY as its new General Manager. With 25 years of expertise in telecommunications, IT infrastructure, networks, and cybersecurity, Dũng LY is committed to instilling a strategic vision for sustainable growth, backed by proven skills to strengthen Ikoula's position in the market.

 Visit
Visit  Naxos
Naxos Markethings
Markethings DataTourisme
DataTourisme